Cyber Resources
Below are some helpful resources regarding cyber security. Click these links to view the articles:
Cybercrime Claims Scenarios: Can These Happen to You?
Healthcare has a Cyber Problem
6 Tips to Prevent Healthcare Ransomware Attacks
Cybercrime Claims Scenarios: Can These Happen to You?
 In a word, yes. Many chiropractors significantly underestimate how much a breach will cost, and think they can self-insure it. Outlining what will happen in the event of a breach is very useful when understanding the value of cyber liability coverage. Below are a variety of claims scenarios that help illustrate the severity of cyber claims, and how widespread cyber breach activities are throughout the healthcare industry.
In a word, yes. Many chiropractors significantly underestimate how much a breach will cost, and think they can self-insure it. Outlining what will happen in the event of a breach is very useful when understanding the value of cyber liability coverage. Below are a variety of claims scenarios that help illustrate the severity of cyber claims, and how widespread cyber breach activities are throughout the healthcare industry.
Scenario 1
Employees of a large chiropractic group discovered that their email accounts were not accessible. The group’s IT department investigated and discovered that a ransomware attack infected 10 servers and 50 workstations. The group had to close operations for two business days and suffered losses in relation to the event.
Cyber insurance covered a total of $83,050, as follows:
- IT Expenses: $59,571 – Consultants were retained to immediately address the ransomware attack, secure data, investigate if any patient health information was compromised, and rebuild the group’s network.
- Business Interruption Expenses: $9,286 – Several appointments had to be cancelled, and could not be rescheduled, resulting in loss of income.
- Data Recovery: $10,857 – Numerous employees had to work overtime to recreate lost data from back-ups.
- Ransom Amount: $3,336 – The group paid the ransom demand to regain system access.
Scenario 2
A provider of in-home chiropractic care was investigated by the Office for Civil Rights (OCR) after receiving a complaint that one of the provider’s employees left behind documents containing the protected health information of 278 patients after moving residences. Evidence supported this complaint. The OCR found that the provider was significantly lacking adequate policies and procedures in place to address the safeguarding of patient information when taken offsite. As a result, the provider was ordered to pay $239,800 in civil money penalties imposed by OCR.
Scenario 3
A mid-size chiropractic group’s network of computers was infected with ransomware, potentially compromising patient data. The group did not pay the ransom and instead focused its efforts on reconfiguring the computer system and restoring the data from backups. Under state privacy laws, the group was required to notify almost 10,000 patients about the breach. Cyber insurance covered the group’s breach notification costs, which totaled approximately $27,500.
Scenario 4
The personal data of over 2,000 credit and debit cardholders was exposed when a chiropractic group with multiple locations learned that 10 of its card readers had been compromised by a rogue employee. Across several of the group’s locations, the readers had been manipulated and credit card data had been “skimmed” to sell on the black market. The group’s bank investigated and found that the group failed to maintain data security controls required under the Payment Card Industry Data Security Standard (PCI DSS). The bank imposed fines and assessment against the group for PCI DSS non-compliance.
If you have any concerns about your cyber coverage and want to know more about what we offer, fill out our online form to get a no-obligation quote.
Source: PICA Insights Blog
Healthcare has a Cyber Problem
From the earliest idea of electronically maintaining patient data in the 1960s, through the development of the first electronic health record (EHR) in 1972, to today’s connected devices and web-based systems, the digital healthcare practice has evolved to provide increased convenience, improved patient care, and lower costs to medical providers. But this electronic access to medical records also brings with it additional risks and obligations to practices.
Before the EHR, the biggest threats to securing medical records were likely fires, water damage, or an unauthorized person getting the keys to the records room. With the growth of the digital practice, the threat is both more varied and more difficult to defend against. Cyberattacks have put sensitive patient data at risk of exposure and the practice at risk of violating state and federal regulatory and privacy laws. Worse, a cyberattack can also put patient care and safety at risk.1
The Patient Safety Impact of Cyberattacks
Any device or system that is connected to the internet is vulnerable to attack and compromise by a determined and knowledgeable attacker. This vulnerability can put healthcare business revenue, patient privacy, and even patient safety at risk. A few recent examples:
- A large scale phishing attack in October 2020 affected six hospitals in the University of Vermont (UVM) Health System resulting in postponed appointments, scheduling problems, delayed chemotherapy and radiation treatments, and weeks-long delays to determine whether cancer biopsies were malignant. The attack began when an unwitting employee on vacation opened a personal email on his work laptop and opened an attachment. The email was from a legitimate local business that had been hacked. When the employee returned and logged into the hospital network, the attackers launched the malware.
- In 2021, researchers at McAfee discovered five vulnerabilities in infusion pumps from B. Braun (one of the largest infusion pumps vendors) that could have enabled attackers to conduct remote network attacks or remotely deliver dangerous levels of medication to patients.
- In February 2024, attackers accessed an unsecured computer server used by Change Healthcare. The attack cut off providers from billions of dollars of revenue, disrupted service at pharmacies across the U.S., and may have compromised the personal data of a third of Americans.
- In early May 2024, attackers staged a ransomware attack on Ascension after an employee unknowingly downloaded a malicious file, enabling the attackers to block access to patient medical records, forcing staff to rely on paper and manual processes to order medical procedures, communicate across separate departments, and keep track of hospital patients’ evolving conditions.
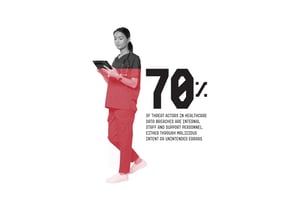
These attacks are not rare and often come from unexpected sources. The employee at UVM who unwittingly launched a ransomware attack, for example, is not alone. The Verizon Business 2024 Data Breach Investigations Report revealed that 70% of threat actors in healthcare data breaches are internal staff, contractors, and support personnel—the highest percentage of the 10 industries studied. A bit of comfort can be taken to know that approximately half of all healthcare breaches were miscellaneous errors, not malicious intent. That means a strong employee cybersecurity awareness campaign in a healthcare organization could dramatically reduce the incidence of successful attacks.



Cyberattacks in Healthcare: Widespread and Costly
When thinking of ways that a cyberattack could affect a healthcare organization, ransomware attacks and data theft likely come immediately to mind for most people because they make headlines. While these are among the most prevalent cyber risks in the healthcare industry, another critical risk is hiding in plain sight: connected medical devices. These ubiquitous IV pumps, blood pressure monitors, EKG machines, and other devices are connected to a practice’s network and often to the internet to store and back up data to cloud services. The statistics are troubling:
- 79% of medical devices in hospitals are used regularly, making them difficult to update.
- 53% of connected devices contain critical vulnerabilities that could jeopardize patient care, safety, or confidentiality.
- 73% of IV pumps in hospitals contain critical vulnerabilities that could jeopardize patient care, safety, or confidentiality.
Connected Medical Devices: Threats Hiding in Plain Sight
“Think of IT security as a chronic illness, a condition that requires ongoing treatment, testing, and re-evaluations. With security, the goal is not an outright cure but a lessening of symptoms, a lowering of risk.”2
In the first half of 2024, the breaches reported to the U.S. Department of Health and Human Services, Office of Civil Rights, affected 45.5 million individuals. That number already eclipses the total for all of 2020 by 30% and (on a prorated basis) will eclipse three of the previous four years. Furthermore, a 2023 study revealed that healthcare organizations experienced an average of 40 cyberattacks in the prior 12 months—88% had at least one.1 The same study revealed that 77% of supply chain attacks, 69% of email/spoofing phishing attacks, 68% of ransomware attacks, 49% of cloud service compromise, and 43% of data loss or exfiltration incidents impacted patient safety and care.1 Despite these threats to patient safety and the $10.93 million average cost of healthcare cyberattacks, only 51% of organizations plan to increase investments in cybersecurity after a breach.
Cyberattacks that block access to patient records, paralyze critical medical devices, and impact patient care are not just an “IT problem” best left to tech experts—they are a patient safety issue. The good news is—because about half of all healthcare data breaches are caused by employee errors—there is an opportunity for a practice to build a pervasive “culture of cybersecurity” and prevent data breaches with a strong program of employee training and awareness. Providers work hard at building a “culture of patient safety” in their practice. Applying that same diligence to building a “culture of cybersecurity” can help employees become aware of their role in guarding against inadvertent cybersecurity incidents and mitigate cyberattacks in general.
1. Ponemon Institute, Cyber Insecurity in Healthcare: The Cost and Impact on Patient Safety and Care 2023, data cited from the full report.
2. Daniel Berger, President and CEO of cybersecurity consultants Redspin, quoted by Diana Manos, “5 Ways to Avoid Health Data Breaches,” Healthcare IT News, February 19, 2014.
Source: ProAssurance ProVisions, August 2024
Tips to Prevent Healthcare Ransomware Attacks
Ransomware attacks are increasing in frequency, so healthcare organizations need to be ready to tackle them. By taking these steps, your clients can lessen the likelihood of becoming a target for ransomware and other cyber threats.
1. Train Employees on Phishing and Data Risks
It is essential to train employees to recognize and report phishing attempts. Staff should be educated on what typical phishing emails look like. To ensure effective training, healthcare organizations should use industry-specific scenarios and real-life examples relevant to their field. Common phishing tactics include:
- Impersonated Email Addresses: Emails that appear similar to your organization’s domain name.
- Requests for Personal Information: Messages asking for sensitive data that employees shouldn’t give out before verifying through alternative methods (such as an authenticated phone call or text).
2. Conduct Vulnerability Assessments
Understanding your vulnerabilities is crucial for preventing ransomware attacks. A vulnerability assessment helps identify and address gaps in your cybersecurity. Healthcare organizations should regularly conduct these assessments to uncover potential weaknesses. When conducting a vulnerability assessment:
- Engage a Specialized Third Party: Choose an external provider with expertise to ensure objective and unbiased results.
- Seek Actionable Recommendations: Some providers may offer limited value if they don’t provide clear steps for addressing identified issues.
3. Implement Multi-Factor Authentication
Multi-factor authentication (MFA) enhances security by requiring multiple forms of verification before granting access. This might include a password along with a fingerprint or PIN. Many healthcare organizations do not currently use MFA for email or remote systems, leaving them vulnerable if a single password is compromised. Implementing MFA reduces the risk of unauthorized access and enhances overall security.
4. Encrypt Computers and Data
Encryption is a fundamental component of cybersecurity. It protects data both at rest (stored on computers or servers) and in transit (when transmitted over networks) by converting sensitive information into unreadable formats without the correct key or password. This ensures that even if data is stolen, it remains inaccessible without proper decryption.
5. Backup Critical Data
Regularly backing up data is crucial to defend against ransomware attacks. Backups can be stored on external hard drives, network storage systems, or cloud-based solutions. It’s important to periodically test these backups by restoring them to confirm their reliability.
6. Require Strong Passwords
Strong passwords are a primary defense against identity theft. Ensure passwords are robust and unique for each account to prevent compromise. To enhance password security:
- Use a Password Manager: This tool can generate and store complex passwords for different accounts, minimizing the risk of using the same password across multiple sites.
- Avoid Password Reuse: Different passwords for different accounts help protect sensitive information from being accessed if one account is compromised.
Reference: The Cyber Research Databank
DISCLAIMER: “OUM” and “OUM Chiropractor Program” do not refer to a legal entity or insurance company but to a program or symbol of a program underwritten, insured, and administered by ProAssurance Insurance Company of America. All statements and opinions on this page are for informational and educational purposes only, they do not establish a standard of care. None of the information presented should be considered as offering legal advice or legal opinion. We are not liable for any errors, inaccuracies, or omissions. Links or references to organizations, websites, or other information is for reference use only and do not constitute the rendering of legal, financial, or other professional advice or recommendations. In the event any of the information presented conflicts with the terms and conditions of any policy of insurance offered by ProAssurance Insurance Company of America, the terms and conditions of the actual policy will apply. All information contained here is subject to change.